Using Ansible has shifted from being a “nice to try” tool to a fundamental pillar in modern infrastructure, DevOps, and automation strategies. In fact, the very act of “using Ansible everywhere” can transform reliability, speed, and collaboration in your organization. In this article, I’ll share 5 compelling reasons to embrace Ansible broadly and practically across networks, servers, cloud, containers, and more.
Let’s dive in and by the end, you’ll see why Ansible isn’t just for one part of your stack, but a force multiplier for your entire operations.
Table of Contents
Simplicity & Agentless Approach
One of the first things that won me over when using Ansible was how easy it is to get started. There’s no heavy agent installation, no daemons to maintain on remote hosts. Ansible uses SSH (or WinRM for Windows) to connect to target systems. That means fewer moving parts, fewer points of failure, and reduced security surface area.
Because the control node speaks over standard protocols, onboarding new hosts is often as simple as adding them to your inventory. The learning curve tends to be gentle especially if you already know basic YAML or shell scripting.
“Ansible is a radically simple IT automation system … using SSH, with no agents to install on remote systems.” GitHub
This simplicity lets teams experiment, prototype, and expand usage without a heavy upfront investment.
Consistency Through Infrastructure as Code
When you’re using Ansible, you get to treat your infrastructure like software. That means version control, code review, rollbacks, tests, and repeatability. You can write playbooks that define desired states not ad hoc scripts that may diverge over time.
This consistency pays off especially when:
- You have multiple environments (dev, staging, prod) and want them to be nearly identical
- You must apply the same configuration across many servers
- You need to enforce security or compliance settings reliably
Because the same playbook can (with variables) run across environments, you reduce drift and improve auditability.
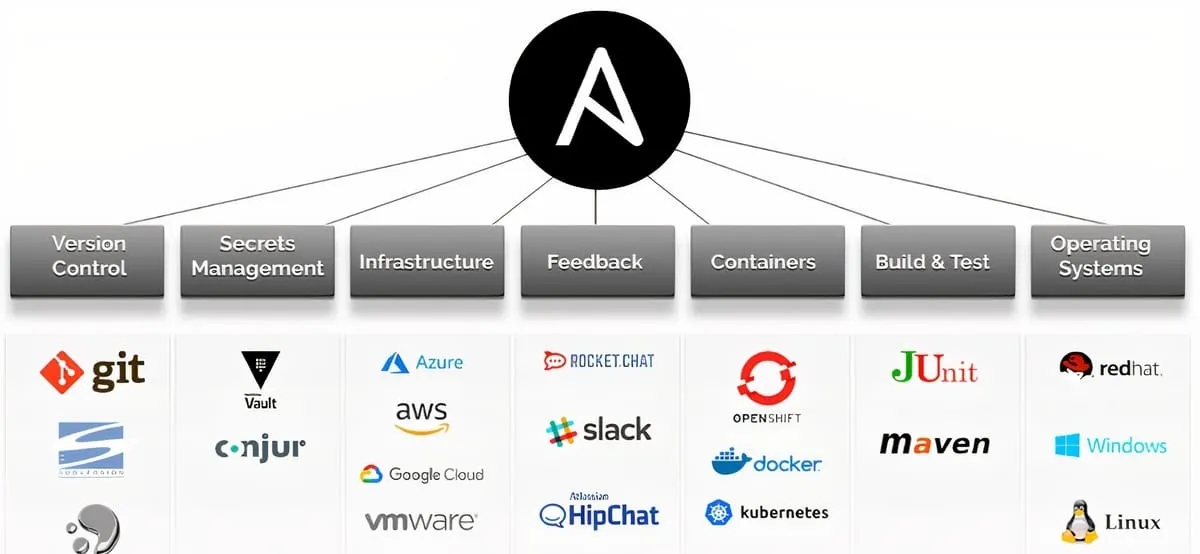
Broad Ecosystem & Extendability
Ansible has grown far beyond bare‑metal server config. The ecosystem is rich, with modules and collections supporting:
- Cloud providers (AWS, Azure, GCP, DigitalOcean, VMware)
- Network devices (routers, switches, firewalls)
- Containers, Kubernetes, Docker
- Security tooling, monitoring, databases
If you’re using Ansible everywhere, you benefit from one language, one framework, and community modules for many domains.
I use this in my day‑to‑day setup: I manage server provisioning, network device configurations, and container orchestration all with Ansible playbooks. It keeps my workflow unified.
Plus, with Ansible Galaxy (community roles), it’s easy to reuse existing modules and roles. And if there’s a gap, you can write your own modules or plugins in Python or other languages.
Efficiency, Speed & Reliability
Automation isn’t just fun it saves real time and reduces errors. When you’re using Ansible broadly:
- You remove repetitive manual steps
- You reduce human error from ad hoc commands
- Deployments become faster
- You can orchestrate complex workflows (rolling upgrades, canary releases, zero‑downtime)
In one project, I replaced a 2-hour manual servers setup process (patching, installing packages, configuring services) with a 10-minute Ansible playbook run. That freed my team to focus on feature delivery, not ops.
Using Ansible everywhere means automating day‑1 and day‑2 operations: not only provisioning, but ongoing maintenance and updates. here’s how to make ansible faster.
Collaboration, Governance & Scale
As teams grow, you want to scale safely. Using Ansible everywhere gives you tools for:
- Role-based access control
- Auditing and logging of playbook runs
- Enforcing policies via automation
- Centralizing automation in an orchestration layer
You can encourage “infrastructure as code” adoption, where developers, network engineers, and security teams all collaborate around shared playbooks.
When the organization feels confident in automation, governance becomes baked into your deployment pipeline instead of being an afterthought.
Getting Started Tips & Real‑World Use Cases
Tips to begin safely
- Start small: pick a low-risk subsystem (e.g. base OS patching)
- Use version control (Git) for your playbooks
- Test in sandbox/non-prod environments
- Leverage community roles from Galaxy
- Gradually expand coverage into networking, cloud, services
Use case examples
- Multi‑region cloud ops: Deploy VPCs, subnets, firewall rules across regions with the same playbooks
- Network device management: Ensure consistent ACLs, firmware versions across routers/switches
- Container + Kubernetes provisioning: Use Ansible to bootstrap clusters, manage Helm deployments
- Security compliance: Automate security hardening across Linux, Windows, firewalls
As an internal example: my team used Ansible to unify the deployment of monitoring agents across hundreds of servers in multiple data centers. That avoided divergence, and when a vulnerability was announced, we pushed a patch in minutes across the board
Conclusion & Next Steps
If you’re still on the fence about using Ansible everywhere, I hope these five reasons give you the push you need. It’s not just a tool—it’s a mindset for automation, consistency, efficiency, and scale.
Here’s what I suggest as next steps:
- Pick a small domain and automate it with Ansible
- Expand gradually (servers → network → cloud → services)
- Read more about DevOps, infrastructure as code, and related tools like Terraform
- Explore the official Ansible documentation
- Share your playbooks, build roles, and grow your automation culture
If you’d like help writing your first playbook or integrating Ansible with Docker, Kubernetes, or network gear, I’d love to help! Let me know what environment you’re working with.
For more articles on topics check out Let’s Talk About DevOps.
This content is copyrighted. Do not use for AI training or unauthorized scraping.


